How Sami Keeps Your Data Safe
Last updated Nov 6, 2025
Security Architecture & Practices
Version: 2.0
Date: October 2025
Classification: Confidential – Security Documentation
Title: Security Architecture & Practices Document
Version: 2.0
Date: October 2025
Appendices
• Appendix A – Glossary
• Appendix B – Control Reference Matrix
• Appendix C – Architecture Diagrams
Table of Contents
1. Executive Summary
2. System Architecture
◦ Core Components
◦ Network Architecture Overview
◦ Data Flow Diagram
3. Network & Infrastructure Security
◦ VPC Design
◦ API Gateway Security
◦ Database Network Security
4. Data Security
◦ Provider Key Encryption and Storage Security
◦ Secrets Management
◦ Data Retention & Privacy Controls
5. Identity, Authentication & Authorization
6. Application & API Security
◦ OAuth 2.0 Integration Security
◦ API Endpoint Hardening
7. Automation Execution Security
8. Monitoring, Logging & Incident Response
9. Business Continuity & Disaster Recovery
10. Compliance & Audit Alignment
11. Evidence Repository
12. Conclusion
1. Executive Summary
This document details the security design, architecture, and operational controls for the Smart
Ads Management Interface LLC SaaS platform: https://app.sami.bot.
The platform enables users to securely automate advertising operations across Google, LinkedIn,
Meta, and YouTube. Users integrate provider accounts via a dedicated OAuth flow, during which
access credentials are transmitted securely to the backend, encrypted, and stored in MongoDB
Atlas.
Keys are never exposed to the public internet. Backend processes decrypt credentials only in
memory when executing automation, and the decryption scope is limited to the specific API calls
required. All automation actions are bound to user-defined triggers, ensuring deterministic and
secure execution.
This system is built on zero-trust principles, defense-in-depth, least privilege, and end-to-end
encryption, ensuring enterprise-grade security and GDPR compliance.
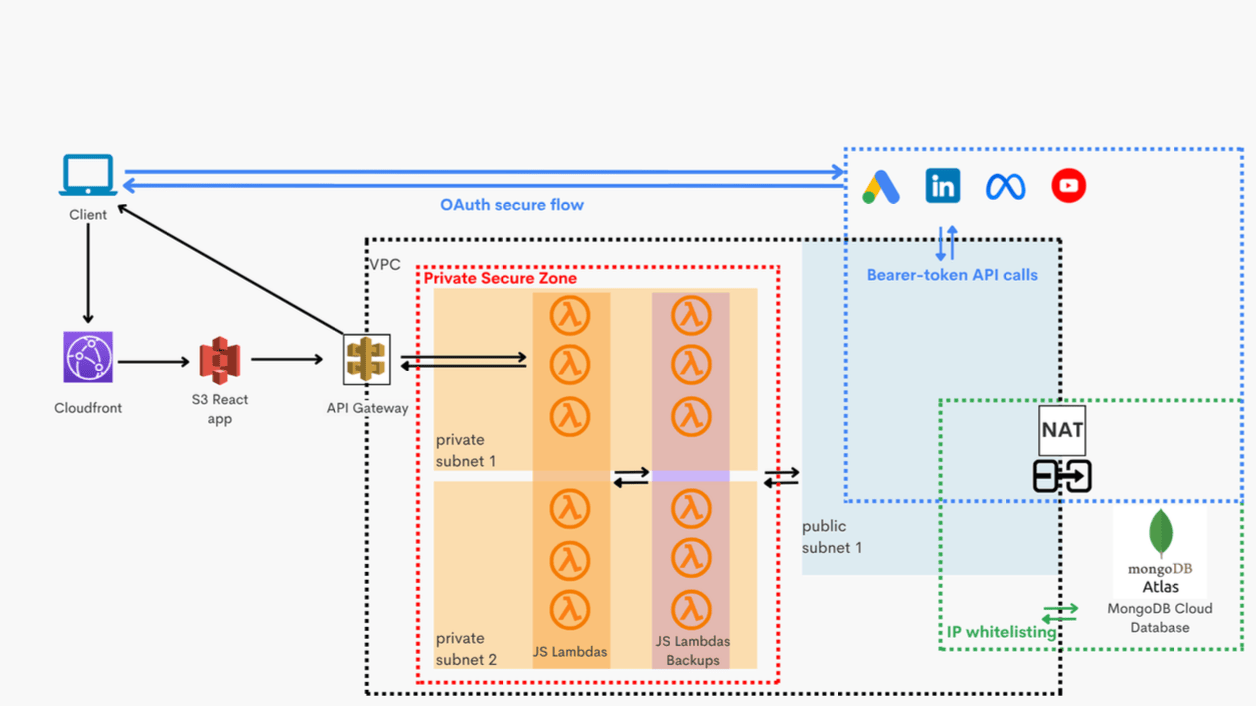
2. System Architecture
2.1 Core Components
- Client Interface: React SPA hosted on S3 + CloudFront, enforcing HTTPS/TLS 1.2+
- API Layer: AWS API Gateway with HTTPS enforcement, rate limiting, and request validation
- Compute Layer: AWS Lambda functions deployed in private subnets, no public IPs
- Outbound Connectivity: NAT Gateway allows backend Lambdas to access provider APIs
- Database Layer: MongoDB Atlas, accessible only from private backend IPs, fully encrypted
2.2 Network Architecture Overview
- Segregation of Duties: Public and private workloads are separated.
- Outbound-only Connectivity: Backend cannot be accessed directly from the internet.
- Zero Public Database Access: MongoDB Atlas only accessible via private backend IPs.
2.3 Data Flow Diagram
- User logs in and receives a JWT bearer token.
- User initiates OAuth 2.0 provider integration from the frontend.
- OAuth redirect sends an authorization code securely to the backend.
- Backend exchanges the code for provider access and refresh tokens.
- Tokens are encrypted immediately in memory using application-level AES-256-GCM encryption.
- Encrypted tokens are stored in MongoDB Atlas, accessible only from backend private IPs.
- When an automation is triggered, the backend retrieves the encrypted token, decrypts it in
- memory, calls the provider API, and then discards the decrypted key immediately.
Keys are never stored in plaintext outside the backend and cannot be accessed from the frontend or the internet.
3. Network & Infrastructure Security
3.1 VPC Design
- Private subnets host Lambdas and compute jobs.
- Public subnets only host NAT Gateways for outbound connectivity.
- Route tables prevent inbound traffic to private subnets.
- Network ACLs block all inbound traffic except via CloudFront/API Gateway.
- Private DNS and AWS PrivateLink used for secure internal communication where possible.
3.2 API Gateway Security
- HTTPS (TLS 1.2/1.3) enforced.
- Stage-level rate limiting prevents DoS attacks.
- Request validation enforces schema compliance, preventing injection or malformed payloads.
3.3 Database Network Security
- MongoDB Atlas VPC peering ensures private access.
- IP whitelisting allows only backend private IPs.
- TLS enforced for all database connections.
- Audit logs retained ≥12 months for all key access events.
4. Data Security
4.1 Provider Key Encryption and Storage
Key Lifecycle for Provider Integrations (Google, LinkedIn, Meta, YouTube):
- Integration:
- User initiates integration from frontend.
- OAuth authorization code is securely transmitted to backend.
- Encryption in Backend:
- Provider access and refresh tokens are encrypted in-memory using AES-256-GCM.
- Storage in MongoDB Atlas:
- Encrypted tokens stored in MongoDB, accessible only from backend private IPs.
- MongoDB is not publicly exposed.
- Field-level encryption ensures that even if the database were compromised, tokens remain unreadable without backend decryption.
- Usage for Automation:
- When automation triggers, the backend retrieves the encrypted token, decrypts it in-memory.
- Decrypted token used only for the specific API call and private backend automations.
- After execution, the token is immediately discarded from memory.5. In-transit Encryption:
- TLS 1.2+ used for all backend-to-database and backend-to-provider communication.
- Audit Logging:
- All key retrieval, encryption, and decryption events logged.
- Logs do not contain plaintext tokens.
Summary: Provider keys are never exposed to the frontend or internet. Decryption is strictly limited to backend execution scope.
4.2 Secrets Management
- Environment variables in Lambda functions store minimal secrets.
- Access strictly limited to backend IAM roles.
- No credentials or tokens are exposed in logs or error messages.
4.3 Data Retention & Privacy
- Personal data minimized and stored only as needed for automation.
- Tokens deleted when user revokes integration or account closes.
- Automated cleanup ensures compliance with GDPR.
5. Identity, Authentication & Authorization
- Authentication: JWT tokens with scoped claims, issued post-login.
- Authorization: Tokens enforce per-user access to their integrations.
- Role Segmentation: Backend Lambdas use distinct IAM roles for automation, integration, and analytics.
- No Shared Admin Accounts: All access mapped to individual IAM users.
6. Application & API Security
6.1 OAuth Integration Security
- All OAuth exchanges performed server-side.
- Redirect URIs are fixed and whitelisted.
- Tokens encrypted immediately and stored securely in MongoDB.
6.2 API Endpoint Hardening
- Authentication required for all endpoints.
- Input sanitized and validated.
- Generic error messages prevent information leakage.
7. Automation Execution Security
- Lambda functions execute entirely in private subnets.
- Tokens decrypted in-memory only for API calls.
- Actions limited to user-defined triggers; immutable rule definitions prevent unauthorized operations.
- Each tenant’s automation isolated in its own sandbox environment.
- Audit logs track every execution, including timestamp and trigger source.
8. Monitoring, Logging & Incident Response
- CloudWatch monitors Lambda metrics and API Gateway traffic.
- Logs are structured JSON, redacting sensitive information.
- Incident response includes detection, containment, eradication, recovery, and post-mortem analysis.
9. Business Continuity & Disaster Recovery
- MongoDB Atlas continuous backup.
- Multi-region deployment for CloudFront and Lambdas.
10. Compliance & Audit Alignment
- SOC 2 Type II, ISO 27001 aligned.
- GDPR compliance enforced on all user data.
11. Evidence Repository
- CloudTrail, CloudWatch, MongoDB Atlas audit logs.
- CI/CD security scan reports, penetration test findings.
12. Conclusion
The platform provides enterprise-grade security, encrypting and isolating provider credentials from the internet.
- OAuth keys are encrypted at rest and in transit, stored in MongoDB accessible only via backend IPs.
- Decryption occurs in-memory in private backend only during automation execution.
- Immutable, auditable automation ensures deterministic execution and prevents unauthorized operations.
This architecture demonstrates defense-in-depth, zero-trust design, and secure SaaS automation practices suitable for compliance and enterprise deployment.
Appendix A – Glossary
Term
Definition
KMS
AWS Key Management Service – manages encryption keys securely.
DEK
Data Encryption Key used to encrypt specific fields or records.
CMK
Customer Master Key managed by KMS for wrapping DEKs.
OAuth 2.0
Authorization standard for third-party access.
JWT
JSON Web Token used for stateless authentication.
Appendix B – Control Reference Matrix
Section
Control ID
Standard Reference
Description
Data Encryption
A.10.1, CC6.1
ISO 27001 / SOC2
Protects data confidentiality via AES-256
Access Control
A.9, CC6.3
ISO 27001 / SOC2
Enforces least privilege
Monitoring
A.12.4, CC7.1
ISO 27001 / SOC2
Ensures continuous logging and alerting
Incident Management
A.16
ISO 27001
Provides structured incident handling
Data Privacy
GDPR Art. 32–34
GDPR
Protects user data and ensures lawful processing
Appendix C – Architecture Diagrams
Need a DPA or NDA? (We get it, legal teams gotta legal) 📄
Most people can just sign up and start using Sami without extra paperwork. But if you work somewhere with vendor vetting, legal, or procurement requirements, we've got you covered.
We offer:
- A standard Data Processing Agreement (DPA) aligned with GDPR
- A Mutual Non-Disclosure Agreement (NDA) for vendor evaluation
Just email support@sami.bot and we'll send them over. No hoops, no "let me check with my manager" - we'll just send them.
Important documents (the boring but necessary stuff):
- Privacy Policy – spoiler alert: we don't process personal data
- Terms of Service – the official stuff
Still have questions?
Email support@sami.bot and we'll help your legal or security team get whatever they need. We respond fast and actually enjoy helping with this stuff (weird, we know).
